Introduction
Open Security Compliance is a standalone rules engine framework that allows customers to automate and orchestrate security rules. Rules can be deployed in a standalone mode in docker and can be executed through a CLI called cowctl. This user-friendly CLI can be used to perform useful utility functions such as initializing and scaffolding, allowing developers to develop, unit test rules for automating, and running them standalone in your docker
environment.
Glossary
| Name | Description |
|---|---|
| ApplicationType | A package for a specific application type that provides reusable methods and validations, which can be imported and used within tasks to perform application-related operations. |
| Task | A task is an automatic unit of work in OpenSecurityCompliance. This can be written in Go or Python, and can be unit tested. |
| Rule | A Rule, which is a collection of tasks, can be mapped to a control in any assessment. When an assessment is run, the mapped rules are executed to assess the controls they are mapped to. |
Things to note
- OpenSecurityCompliance has a folder named
catalog, which in turn contains the sub-foldersglobalcatalogandlocalcatalogwhere we store the rules, tasks, etc.- The
globalcatalogserves as a folder for publicly accessible rules, tasks and other related components. - By default, rules, tasks, and other artifacts (except the application classes and the credential classes) are initialized in the localcatalog. To maintain code privacy, you can include this folder in the gitignore file.
- To precisely choose an item from the globalcatalog or initialize an item within the globalcatalog, utilize the
--catalog=globalcatalogflag. - A rule present in globalcatalog won't be able to access a task from localcatalog while the other way is possible.
- The
- cowctl CLI has Minio as a dependency. Minio is required to manage all the file outputs from tasks.
- Changes to environment values, located within the
etcfolder in the form of environment files, will take effect only upon restartingcowctl.
Setting up cowctl CLI
If you've already set up the CLI, you can skip this section and proceed by executing sh run.sh (in Mac or Ubuntu) or ./windows_setup/run.ps1 (in Windows). Then enter cowctl to access the command line interface.
While the CLI functionality on Windows has been partially tested, it may not yet offer full stability or support.
Prerequisites
The cowctl CLI is tested/certified in:
- Mac (Min version: Monterey)
- Ubuntu (Min version: 22.04.3)
- PowerShell in Windows (Min Version: 11)
Please make sure to have the following installed in your machine.
- Docker (v24.0.6 or higher)
- In case of Windows, you might need WSL2 too, with Hyper-V enabled.
- Docker Compose (v2.22.0 or higher)
- Python (v3.10 or higher)
- Golang (v1.21.3 or higher)
- yq (to process YAML, JSON, XML, CSV and properties documents from the CLI). Refer to the yq GitHub page for the install instructions.
Instructions
-
Clone the OpenSecurityCompliance Repo.
-
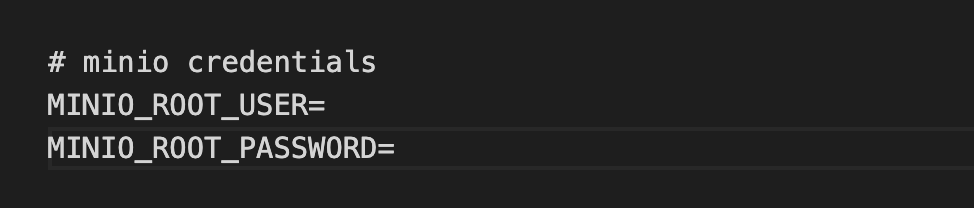
Since OpenSecurityCompliance utilizes a containerized Minio instance, you need to configure Minio with credentials, by setting up username and password of your choice, within the
etc/policycow.envfile.
- If you are running this on a Linux machine, please make sure to update the docker-compose file (
docker-compose.yaml) and comment the specified lines (as shown below).
![]()
-
Rename the
.credentials.env.templatein theetc/folder to.credential.env. This env file which contains predefined credential values, can be used to configure additional credentials for your custom applications. These credentials will be available as environment variables that can be used in your tasks. -
To start the cowctl docker container, run the
build_and_runscript in the OpenSecurityCompliance main folder (as explained in the OS specific collapsibles below). This step typically requires anywhere from 5 to 10 minutes to finish. In case you run into any errors related to loading metadata for certain libraries, rename the keycredsStoretocredStorein the docker config file in your system (For instance in Mac:~/.docker/config.json). This is a known issue in Docker. Note: You may have to restart docker.
Mac or Ubuntu
sh build_and_run.sh
Windows (PowerShell)
./windows_setup/build_and_run.ps1
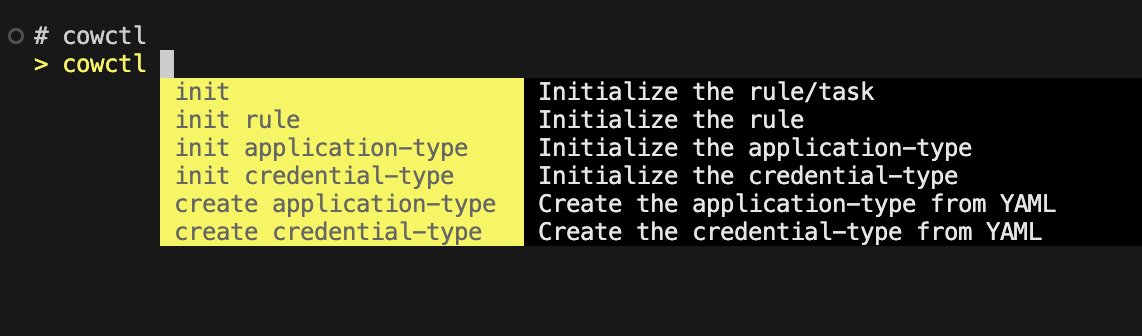
- Once it is built, type
cowctland you will get in to the prompt (as shown below).- Explore the Command & Flag suggestions by typing
--helpor-h. - You can filter names from a list of names using the "/" key when using commands such as
cowctl exec. - Type
exitto get out of the cowctl prompt any time.
- Explore the Command & Flag suggestions by typing